Have you tried any of the erasing utilities on the market? If you have, then you must have noticed that most of them do not offer a real control over the wiping process. They usually offer only two types of destroying (wiping) information: a normal (one or two pass) wiping and a special U.S. DoD seven pass wiping. You may find that in some cases none of the above two options is appropriate for you. What can you do in this case?
Eraser does not only let you choose from several (14) built in wipe methods, but it also offers an easy way to define (create) your own wipe methods. Defining a wipe method means specifying the number of passes and the overwriting pattern for each pass.
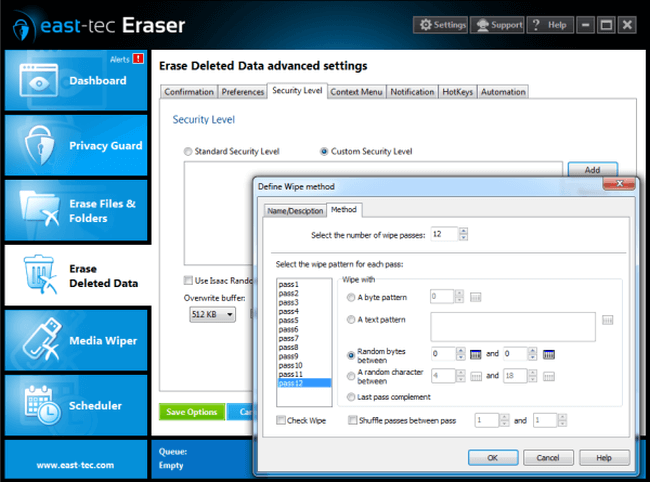
The number of passes specifies how many times to overwrite the data. One pass is sufficient to stop software recovery tools. Several passes might be needed to stop hardware recovery tools such as electron-tunneling microscopes. These tools can recover faint magnetic residue from previous writes.
The overwriting pattern (or the wiping pattern) is the pattern used to overwrite the file data. You can choose between:
- a fixed byte pattern (e.g. 0, FF, etc.)
- a text pattern (e.g. "Censored by Me!")
- a random data stream
The Shuffle passes option is used to mix the order of the passes indicated by the interval defined by the two values. To use this option, you need to select at least 2 wipe passes.
A very powerful security feature is the possibility of verifying whether the wiping patterns are written correctly to disk over the file's original data. This is accomplished by re-reading the data from file after each pass and comparing it with the wiping patterns.
IMPORTANT: If you want to wipe a file located on a compressed drive, the selected wipe method must have at least one pass that uses a random data stream. A random data stream cannot be compressed, therefore you are assured that the entire file is properly overwritten.
