When you use social media services, or applications, like Facebook, Twitter, Google+, Skype, Yahoo Messenger, etc, your activities leave traces not only on your profile pages, but in your browsers and on your computer's hard drive, too.
Trouble is, many of these traces remain on your computer even if you delete your activity traces from your profiles. For instance, you may delete a conversation from your Facebook page, but your computer still stores evidences of your conversation.
If unauthorized parties access your computer, they can find out about your social media activities by following the revealing trails you left behind.
Let's have a look at some of those sensitive trails and let me show you how to securely remove them.
Browsers
History
- URLs of social media sites visited
- Names of friends, or people whose photos, or profile pages you viewed
- Names of friends, or people you chatted with
- Names of friends or people you searched for
- Image/photo captions
- File-names and locations of photos, videos, music files, docs, apps, etc you downloaded from social media sites
Cache
- Locally stored copies of frequently visited social media pages
- Images, texts, music files from frequently visited social webpages
- Details of chat history
Cookies
- Advertising cookies based on on your profile information (age, gender, country of residence, DOB, etc)
- Browser cookies (URLs of visited sites and your unique identifiers for the services)
Search history
- Your computer remembers every single search query you have ever entered into search fields including those when you were looking for sites, people, files, etc, related to social media
Windows
- Skype history: Contents of your chat conversations, info about your calls, messages, sent and received files, etc
- Recent Items folder: File-names, locations, paths of downloaded files and date/time of downloadings
- Temporary Internet Files: Webpages are locally stored here (on your hard drive) for fast loading. Logged data include: URLs of visited social media pages, cookies, images/photos, text files, icons, etc
- If you use third party applications (such as, image organizers, doc editors, multimedia apps, etc) to handle (open, view, watch, listen to, edit, save, send, etc) files you have downloaded, or intend to upload to social media, Windows logs info about your activities
Comprehensive protection
To protect your privacy, east-tec Eraser can permanently remove such tracks and sensitive files from your hard drive and browsers. It destroys your browsing, search and download history, cookies, cache, form data, autofill data, the content and information about your chat conversations, the sensitive images, videos, sound files, or docs you downloaded/uploaded and more.
I. How do I wipe sensitive social media activity traces from my computer, browsers and applications?
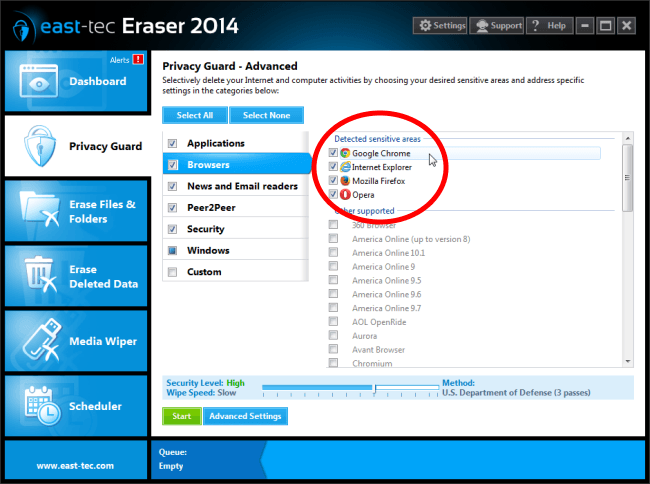
To destroy activity traces from your browsers, third party applications and Windows, it only takes a couple of steps to configure east-tec Eraser. It is so because east-tec Eraser was designed to automatically detect and remove sensitive tracks from the following major sensitive areas of your computer: Applications, Browsers, News and Email readers, Peer2Peer, Security, Windows 8 Apps, and Windows.
Supported browsers include: Google Chrome, Mozilla Firefox, Internet Explorer, Opera, Safari, Maxthon, and many more. Supported applications include: Skype, Google Talk, Yahoo Messenger, MSN Messenger/Windows Live Messenger, AOL Instant Messenger. Your social networking activity traces on services, such as, Facebook, Twitter, G+, LinkedIn, etc, will be securely removed from your browsers and hard drive.
To get started, run the program and click Privacy Guard. Run Basic to start a thorough wipe on all the sensitive areas of your computer without any configuration needed on your part.
Important note: Close your browsers and applications to be wiped before starting the wiping process!
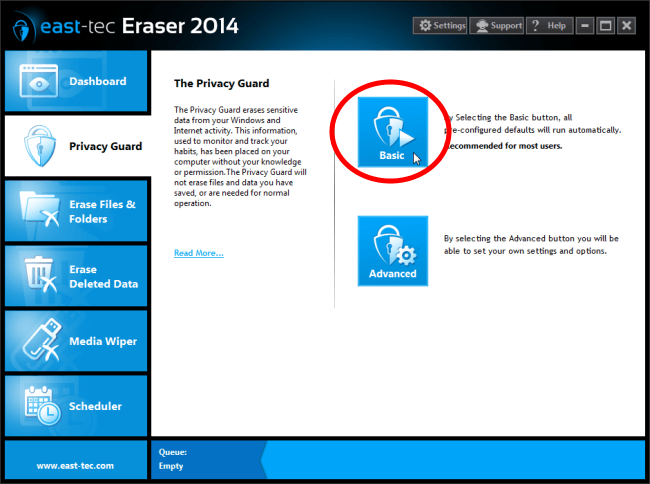
Once the wipe is finished, you can be rest assured that your activity traces are securely removed from your computer beyond forensic recovery as east-tec Eraser employs government-grade wiping methods for the secure destruction of sensitive data.
However, if you sync multiple computers (home desktop PC, business laptop, your spouse's laptop, etc) wiping your sensitive activity tracks from only your primary device won't fully protect you! Your browsing history, download list, login details, bookmarks, settings, etc, all get synced between your devices so you need to wipe them from all the connected computers! Learn more about the issue here.
The Advanced option lets you configure additional privacy settings for each sensitive area.
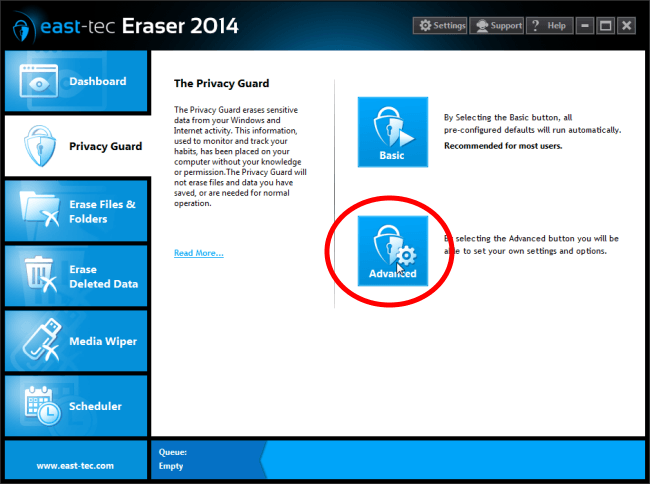
You may, for instance, want to prevent certain cookies from being erased, or wipe sensitive tracks from selected, or all user profiles in a browser. You can configure such settings in any browser installed on your computer.
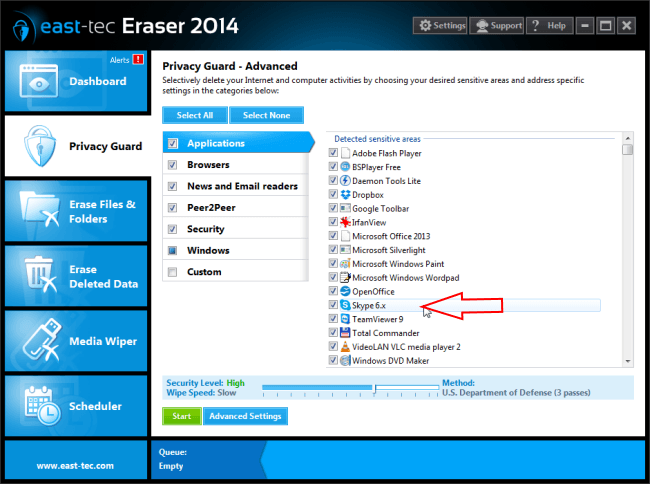
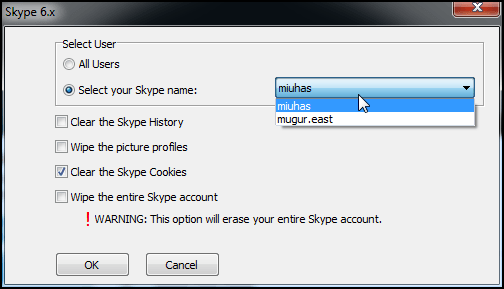
You may want to configure the activity traces wiped from third party applications. Let's say you handled sensitive Facebook images with Picasa so you want to wipe its cache. Or, you want to securely erase the content and traces of confidential Skype chat conversations from your accounts. You can configure and erase multiple traces from every application installed on your computer. As you can see below, it's easy to select and configure applications. We picked Skype for the demonstration.
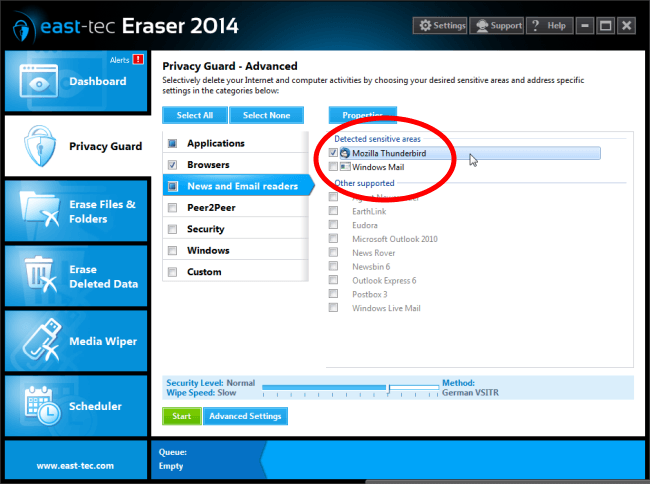
The Advanced feature also helps you get rid of sensitive, locally stored emails for good, from popular clients, such as, Mozilla Thunderbird, Windows Mail and more.
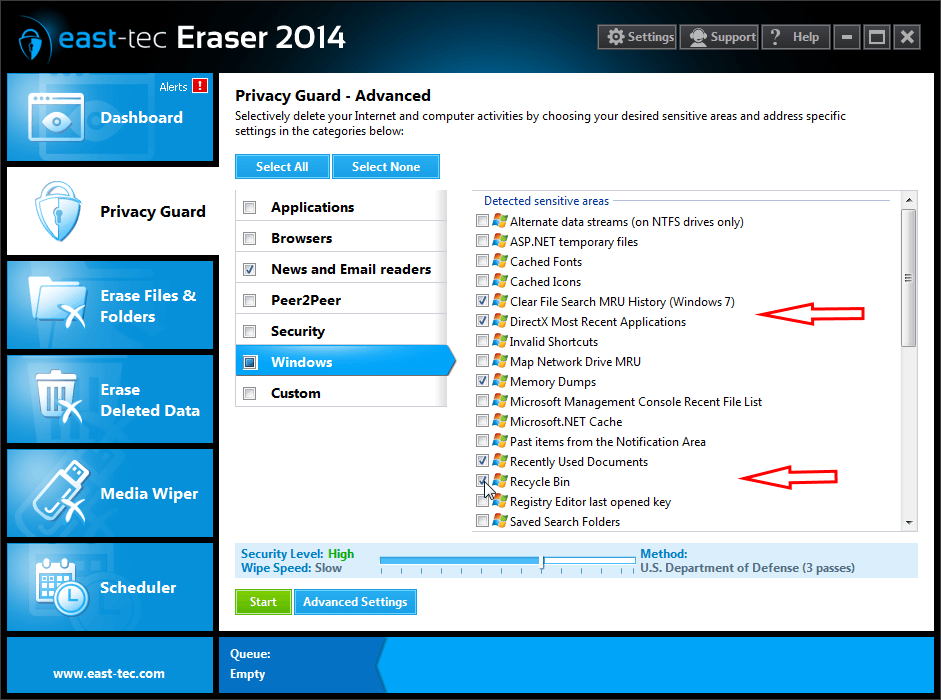
You can also securely remove sensitive tracks Windows logs about your activities, such as, files from the Recycle Bin, the list of Recently Used Documents, Files and Folders, Temporary Internet Files and more.
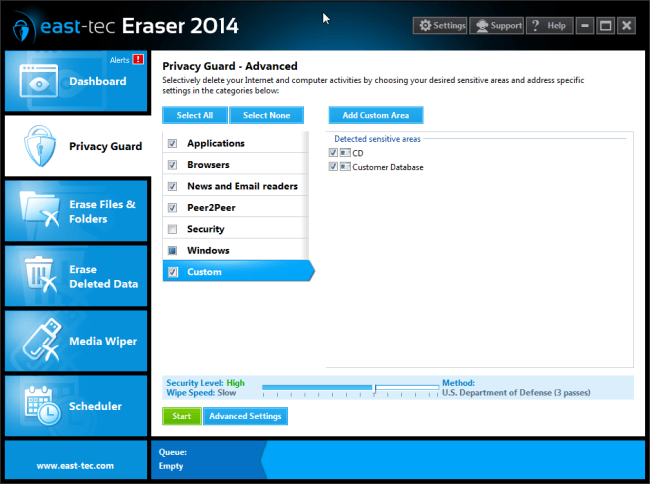
You may also custom select files and folders to be automatically erased when a wipe is run. Here you can include files and folders a general wipe wouldn't touch, for instance, your personal files/folders.
II. How do I wipe sensitive social media files from my computer?
If you would like to get rid of sensitive images, photos, videos, sound files, documents downloaded from, or uploaded to social media services, please follow the steps below.
-
Select the "Erase Files & Folders" module from the main menu. Click "Add files and Folders" to select the files/folders you would like to destroy.
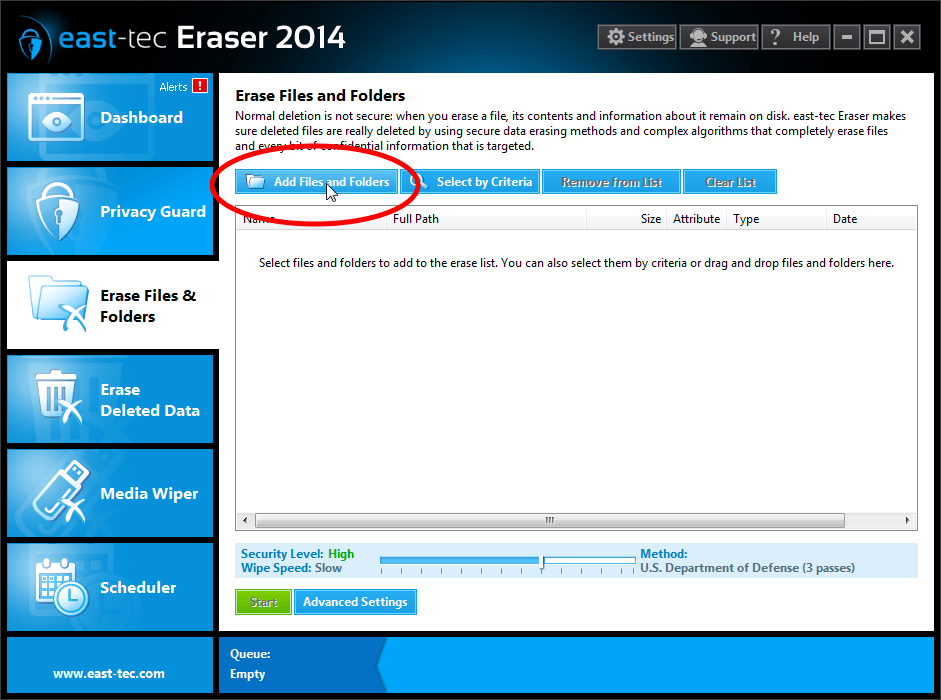
-
Windows Explorer opens so you can easily locate the files/folders to be wiped.
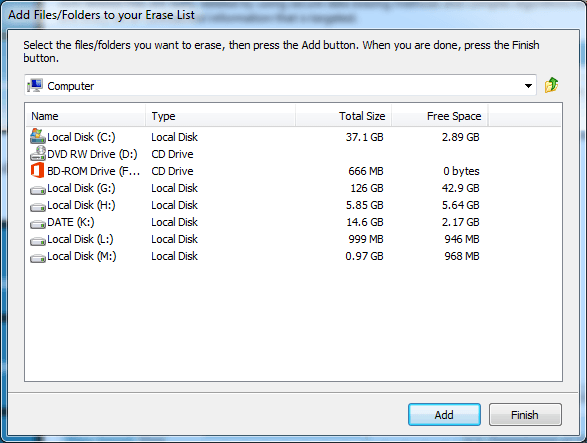
-
Confirm a selection by clicking "Add". Keep adding as many files/folders you need. Click "Finish" when done adding.
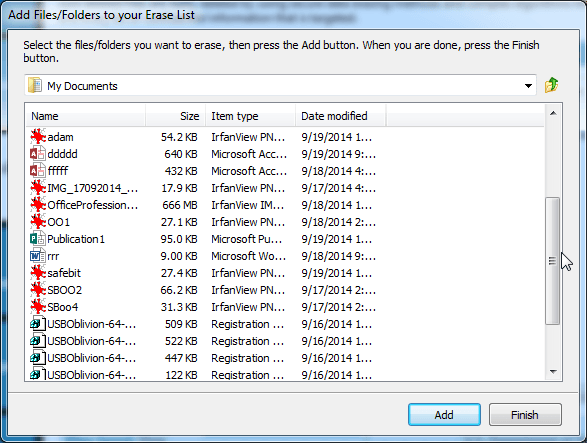
-
You are back in the main windows where you can see that your selected files/folders have been added to the erase list. Click "Start" to begin the erasure action.
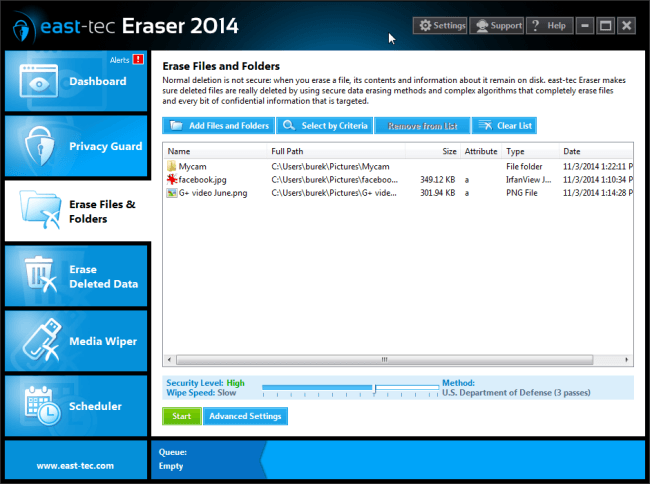
-
That's it! Your sensitive files/folders are now gone beyond forensic recovery since east-tec Eraser employs government-grade wiping methods for the secure destruction of confidential data.
Using the privacy techniques mentioned above you can securely remove the traces of your social media activities.

